Security company, FireEye, has announced a new threat protection platform designed to help enterprises deploy new security models to counter modern cyber attacks.
Many traditional defences, such as firewalls and anti-virus, are not enough to counter the more advanced nature of today’s cyber attacks, leaving the majority of enterprises compromised, the company states.
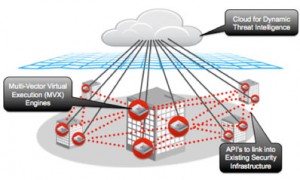
The FireEye platform creates a cross-enterprise threat protection fabric using a next-generation threat detection engine, dynamic threat intelligence, and interoperability with a broad ecosystem of more than two dozen technology alliance partners to secure all major threat vectors and enable rapid detection, validation, and response to cyber attacks.
“We constantly monitor the cyber threat landscape and perform in-depth analysis of emerging threats,” said Jon Ramsey, Chief Technology Officer at Dell SecureWorks. “The FireEye platform, along with the data it provides, is an integral component of our end-to-end life cycle approach to protecting Dell SecureWorks customers from advanced threats.”
The FireEye platform unifies many security technologies to help enterprises modernise their security strategies. The platform is formed by three core components that work in concert.
The first is the Multi-Vector Virtual Execution (MVX) Engine – The MVX engine is designed to capture and confirm today’s cyber attacks by detonating Web objects, files, suspicious attachments, and mobile applications within instrumented virtual environments. It is the leading signature-less technology that can be used across threat vectors to automate the discovery and forensic analysis of malicious code resulting in multi-vector dynamic threat intelligence on attacks specific to an organisation. By correlating multi-vector dynamic threat intelligence for a particular enterprise, customers can block infiltration mechanisms used by advanced persistent threats (APTs).
The second is the Dynamic Threat Intelligence (DTI) Cloud – Subscribers to the DTI cloud exchange the latest multi-vector threat intelligence on new criminal tactics, developing APT attacks, and malware outbreaks. By exchanging anonymised threat intelligence through the DTI cloud, participants gain contextual visibility of global attacks and can strengthen their collective security with the latest protections and neutralise attacks before they cause catastrophic damage.
And the third is the Partner Interoperability via APIs and Standards-based Threat Intelligence Metadata – Partner integrations utilise the FireEye APIs to address the network visibility, endpoint validation, and enforcement options needed by today’s organisations. In addition, FireEye will be publishing a standards-based threat intelligence metadata exchange format that enables FireEye and third-party security solutions to interoperate and automate key cyber security workflows. The metadata format will enumerate malware attributes, actions, and forensics captured in our MVX engine. As a result, customers can better leverage their existing infrastructure and achieve greater security ROI.
“Organisations are looking for an easier way to confirm suspected incidents so they can rapidly resolve them,” said Dave Merkel, CTO of Mandiant. “By utilising our integrated platforms, security teams can connect the dots between what is happening on their network and their endpoints. This eliminates blind spots and creates the complete picture required to fully scope and contain security breaches as they are unfolding.”
“FireEye is the security platform organisations can rely upon for protection against today’s new breed of cyber attacks,” said David DeWalt, FireEye Chairman and CEO. “We have enabled flexible options so customers can integrate our dynamic threat intelligence into their existing security infrastructure to automate the threat response and rapidly neutralise today’s cyber attacks.”
The FireEye Global Industry Alliances Program supports interoperability to build a next-generation threat protection infrastructure based on the FireEye platform. The FireEye programme features technology partners in several categories.
* Perimeter – Existing network gateways can be used for enforcement actions or advanced quarantine of endpoints, such as restricting access to sensitive information in databases and file servers. Partners include A10 Networks, Blue Coat Systems, Bradford Networks, Juniper Networks, and Netronome.
* Monitoring/SIEM – Reporting and SIEM partners enable consolidated reporting and enterprise security integration capabilities. Partners include HP ArcSight, IBM Q1 Labs, RSA, and Splunk. Network aggregation and full packet capture partners offer flexible deployment and contextual analysis options. Partners include Gigamon, Ixia Anue, RSA NetWitness, Solera Networks, and VSS Monitoring.
* Endpoint - Endpoint security partners provide endpoint visibility, validation, and remediation capabilities. Partners include Mandiant, Bit9, Guidance, McAfee, and Sophos.
* Managed Security Service Provider (MSSP) – MSSP partners provide malware expertise and minimise the IT complexity and costs associated with owning and managing their own IT infrastructures. Partners include Dell SecureWorks and Solutionary.
